WASHINGTON — The U.S. Department of Defense on Tuesday unveiled its zero-trust strategy and road map, highlighting how the department plans to shield sensitive information from prying eyes.
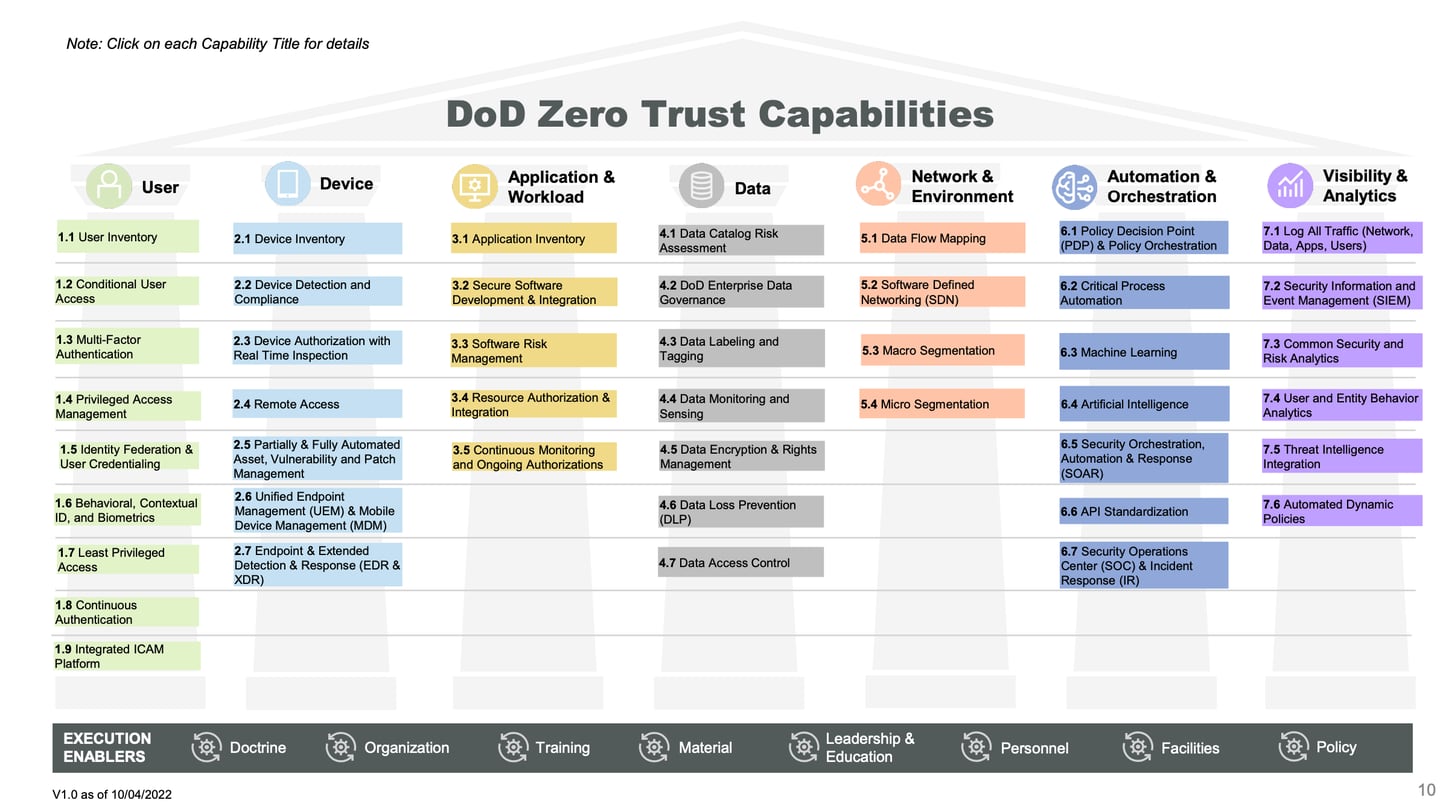
The documents detail the more than 100 activities, capabilities and pillars needed to achieve zero trust, a new paradigm for cybersecurity. The strategy fits into a larger constellation of security planning that includes the recently released National Defense Strategy, officials said.
“If we compare this to our home security, we can say that we traditionally lock our windows and doors, and that only those with a key can gain access,” Randy Resnick, the director of the zero trust portfolio management office, told reporters Nov. 22. “With zero trust, we have identified the items of value within the house and we’ve placed guards and locks with each one of those items inside the house, as well.”
Unlike older cybersecurity models, zero trust assumes networks are always at risk or are already compromised. As a result, continuous validation of users, devices and access is required. Pentagon Chief Information Officer John Sherman has likened it to trusting “no one or no thing.”
RELATED

The transition to segmentation and inherent distrust comes as the U.S. prepares for a potential fight against China or Russia — world powers with histories of cyber aggression. Russia has deployed cyberattacks against Ukraine in its latest invasion, Western authorities say, and China leverages the digital domain to siphon intellectual property for its own gains.
The Defense Department has since 2015 experienced more than 12,000 cyber incidents, with yearly totals steadily declining since 2017, according to a Government Accountability Office evaluation. The federal government in early October said hackers infiltrated a defense industrial base organization, maintained “persistent, long-term” access to its network and absconded with sensitive data. The victim — most likely a defense contractor — was not named.
“Cyber threats and attacks are evolving at an ever-increasing pace and requiring a coordinated, defensive response that is adaptive, flexible, and agile,” the zero-trust strategy states. “Traditional perimeter or ‘castle-and-moat’ security approaches based on conventional authentication and authorization models do not work effectively to thwart current (and future) cyber-attack vectors.”
Defense officials previously imposed a five-year deadline to implement zero trust. The strategy maintains the fiscal 2027 timeline, which cybersecurity leaders described as challenging but important.
“Implementation of our zero-trust goals, to include educating every corner of the department, is an ambitious undertaking,” acting Principal Deputy Chief Information Officer David McKeown said. “We recognized that from the beginning, and that has driven our pace and informed our strategy.”
The Defense Information Systems Agency in late July extended a zero-trust agreement known as Thunderdome with Booz Allen Hamilton, the 22nd largest defense contractor in the world by revenue, according to a Defense News analysis.
DISA at the time cited lessons learned from Russia’s attack on Ukraine and the need to further harden the Secure Internet Protocol Router Network, or SIPRNet, a means of relaying secrets.
DISA, the Pentagon’s lead IT agency, in January awarded Booz Allen the $6.8 million contract to develop a Thunderdome prototype. The subsequent extension stretches the pilot to a full year, with completion now expected at the start of 2023.
The Defense Department in 2021 decided to sunset Joint Regional Security Stacks in favor of the zero-trust Thunderdome approach, C4ISRNET reported.
Colin Demarest was a reporter at C4ISRNET, where he covered military networks, cyber and IT. Colin had previously covered the Department of Energy and its National Nuclear Security Administration — namely Cold War cleanup and nuclear weapons development — for a daily newspaper in South Carolina. Colin is also an award-winning photographer.








